CSS3 Side-Channeling Attacks De-anonymizes Facebook Users
CSS3 Side-Channeling Attacks De-anonymizes Facebook Users
Online anonymity and protecting private information is in the forefront of IT security. Facebook CEO Mark Zuckerberg was under fire after from US Congress for security leaks that had occurred with the data firm Cambridge Analytica. But recent findings have found that data sharing amongst advertisers is not the only concern. Exploiting the recent additions to CSS3 can be used to de-anonymize social media users in a side-channeling attack.
The staggering additions added to CSS3 and HTML5 increased the attack surface of browsers and increasing the risk of security holes. Google security researcher Ruslan Habalov in collaboration with Dario Weißer found an exploit with CSS3’s “mix-blend-mode” that can leak information from other sites.
The vulnerability was discovered by assessing the DOM of the CSS iframe which includes a cross-origin resource though usually forbidden by default. Since the iframe shows the content from the linked site, the researchers tested various CSS features to see if it would leak state information with interactions with browser features. They found that the “mix-blend-mode” has a bug that can be used for side-channel attacking.
The side-channeling attack works as follows: 1) a large stack of DIV elements with “mix-blend-mode” is overlayed on a target iframe with cross-origin. 2) The color of the underlying pixel can be determined by the amount of time it takes to render the DIV stack. 3) Moving the DIV “scan” stack across the iframe to measure the rendering times reveals the iframe’s content.
Similar attacks such a clickjacking are mitigated by JavaScript iframe busters and http header X-Frame-Options. However, this side-channeling attack still leaves personal data vulnerable while a user is logged onto a social media account. In a proof-of-concept, Habalov and Weißer have demonstrated here:
https://www.evonide.com/wp-content/uploads/2018/05/image2.gif
https://www.evonide.com/wp-content/uploads/2018/05/image4.gif
The attack took 20 seconds for the username, 5 minutes for the profile picture and 500 milliseconds for all sites that they liked. Due to the JavaScript performance APIs, this style of attack was limited to 1 bit per 16ms (60 Hz).
The CSS blend mode is similar to what is found in Photoshop or Gimp and allow stacked layers to interact in an abundance of ways. For example blend will interact with cross-origin iframes and multiply the colors to compute a new color such as: color(bottom_layer) × color(top_layer) = new_color, or in terms of rgb (255, 255, 255) and (255, 0, 0) will result in (255, 0, 0). Though a simple multiply function will always amount to the same computation time independent of the underlying content, more computation intensive blend modes would reveal the necessary re-rendering times such as “saturation.” The researchers provide a pseudocode as follows:
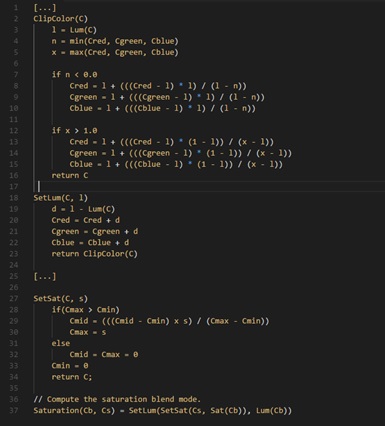
It is important to note that the complexity compared to multiply operation and using different branches depending on the input colors. This forces different rendering times for different colors, revealing which starts to reveal which colors are being used. To reveal black pixels, several Saturation layers were stacked on a preprocessing stage:
|Saturation|
|Saturation| Trigger delay (>200 layer)
|Saturation|
|Preprocess|
|Cross-Origin Iframe| (target pixel)
The saturation layers are the same applying saturation blend mode with enough layers to cause a measurable delay in rendering time. Because the iframe pixel can have an arbitrary color, the saturation stack cannot be passed directly to it.
A more in depth coverage of the exploit is described at the researchers report in the link above. It is important to note that the recent Meltdown and Spectre virus showed that side-channel exploits are hard to patch. Habalov and Weißer note, “We have only demonstrated the attack potential against Facebook. However, throughout the web there are tons of other sensitive resources which could be affected by attacks like this in a similar fashion.” While this only scratches the surface of CSS3 features, it already exposes the potential of how much information can be leaked from social media. We should expect more exploits to reveal itself in the future.
Original Article: https://www.evonide.com/side-channel-attacking-browsers-through-css3-features/


